The digitalization of energy systems brings unprecedented opportunities for efficiency and flexibility—but it also introduces new vulnerabilities. As more Internet of Things (IoT) devices and Distributed Energy Resources (DER) connect to the grid, attackers gain potential entry points to disrupt operations. Within the eFORT project, researchers at Universidad Pontificia Comillas have been investigating these risks for European power systems, publishing two scientific articles:
Rodríguez Pérez, N., Matanza, J., Sigrist, L., Rueda Torres, J.L., López, G., MaDIoT 3.0: Assessment of Attacks to Distributed Energy Resources and Demand in a Power System. IEEE Open Access Journal of Power and Energy. Vol. 12, pp. 552 – 563, 2025.
Rodríguez Pérez, N., Matanza, J., Sigrist, L., Rueda Torres, J.L., López, G., Confronting the threat: analysis of the impact of MaDIoT attacks in two power system models. Energies. Vol. 16, nº. 23, pp. 7732-1 – 7732-12, December 2023.
The attacks under analysis were:
- MaDIoT attacks—cyberattacks that manipulate electricity demand through compromised IoT devices.
- MaDIoT 3.0 attacks—a new class of attacks that simultaneously target demand-side IoT devices and DER, such as solar PV systems.
Why MaDIoT Attacks Matter
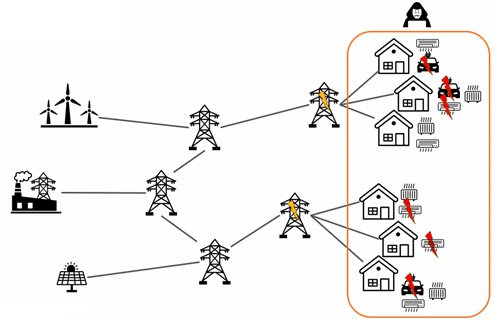
Modern power systems are increasingly dependent on digital technologies and connected devices. While this connectivity enables smart grids, demand response, and consumer participation, it also creates a larger attack surface. IoT devices—such as electric vehicle chargers, smart thermostats, and home appliances—often lack robust security features. Many use default passwords, outdated firmware, or insecure communication protocols, making them easy targets for hackers.
A MaDIoT attack leverages these vulnerabilities by coordinating thousands or even millions of compromised devices to alter electricity demand suddenly. This is not a theoretical risk: the infamous Mirai botnet attack in 2016 demonstrated how millions of IoT devices could be hijacked to disrupt internet services. In the energy sector, similar tactics could destabilize the grid.
Why is this so dangerous? Power systems operate under tight stability margins. A sudden surge in demand can:
- Trigger frequency deviations: If demand rises sharply, system frequency drops. If it falls too low, generators and loads disconnect automatically to protect equipment.
- Activate protection schemes: Mechanisms like Under-Frequency Load Shedding (UFLS) disconnect loads to restore balance, while Over-Frequency Generator Rejection (OFGR) trips generators if frequency rises excessively.
- Cause cascading failures: In extreme cases, these disconnections can propagate, leading to widespread blackouts.
Comillas’ research compared the impact of MaDIoT attacks on two benchmark systems:
- IEEE 39-Bus system (New England, USA)
- PST-16 system (simplified European model)
The findings were striking:
- In the IEEE 39-Bus system, attacks compromising more than 150,000 devices almost always succeeded in triggering protections.
- In the PST-16 system, success ratios were lower (max ~30%), but when attacks succeeded, the impact was severe—up to 20% of demand disconnected, causing rotor angle instability and voltage collapse.
This means that success probability and impact are not the same. Smaller systems may be easier to destabilize, but larger systems can suffer catastrophic consequences under worst-case conditions. Moreover, attackers do not need deep knowledge of grid topology to cause harm—randomly targeting nodes during peak demand can still yield high success rates. As IoT adoption accelerates, MaDIoT attacks could become a real-world threat unless proactive measures are taken to secure the access to these devices.
Going Beyond Demand: MaDIoT 3.0 to Attack Demand and Generation
The second study carried out introduced MaDIoT 3.0 attacks, which combine demand-side manipulation with DER disconnection. As distributed solar PV becomes more common, attackers could exploit vulnerabilities in inverter controls or communication protocols to disconnect generation while increasing demand elsewhere.
Using the PST-16 model with 10% distributed solar PV penetration (representative of expected conditions in Southern Europe by 2030), simulations revealed:
- DER improves resilience against MaDIoT 1.0 attacks: Higher initial voltages reduce success ratios and impact compared to systems without DER.
- Combined attacks (MaDIoT 3.0) remain dangerous: When demand and DER are attacked together, success ratios increase significantly—especially if demand is concentrated in a few nodes. In one scenario, disconnecting 546 MW of solar PV and attacking 1.5 GW of demand caused a voltage collapse, disconnecting 2.85 GW of generation and 15% of demand.
Interestingly, the distribution of attacked demand matters more than DER. Concentrating demand attacks on three nodes had a greater destabilizing effect than spreading them across six nodes, even when the total power compromised was the same.
Key Insights for Grid Resilience
These studies highlight several critical points for operators, policymakers, and technology providers:
- IoT and DER security must be prioritized: Vulnerabilities in consumer devices and inverter controls can cascade into systemic risks.
- Attack success depends on system characteristics: Grid size, topology, and operational conditions influence both probability and impact.
- DER integration changes the game: While DER can improve resilience against certain attacks, it introduces new attack vectors that must be secured.
- Regulatory frameworks are evolving: Initiatives like the EU Cybersecurity Certification Scheme (EUCC) and the Network Code on Cybersecurity set minimum requirements for device security and cross-border risk management.
What Can Be Done?
Mitigation strategies include:
- Secure-by-design IoT and DER devices: Enforce cryptographic firmware updates, authentication, and encryption.
- Advanced intrusion detection systems: Use AI-driven algorithms and edge computing for real-time anomaly detection.
- Collaborative cybersecurity governance: Implement information-sharing protocols under NIS2 Directive and sector-specific network codes.
- Operational resilience measures: Develop coordinated response plans between DSOs, TSOs, and DER operators.
Looking Ahead
Cybersecurity in energy systems is no longer a niche concern—it is becoming a strategic pillar for the energy transition. As grids evolve into complex cyber-physical systems, the stakes are higher than ever. A single vulnerability in a consumer IoT device or a distributed solar inverter can ripple through the entire network, affecting millions of users and critical infrastructure.
The challenge lies in balancing innovation with security. Digitalization enables flexibility, demand-side participation, and integration of renewables, but every new connection is a potential entry point for attackers. This means cybersecurity must be embedded at every layer—from device design to system operation—rather than treated as an afterthought.
Research within eFORT is paving the way for a deeper understanding of these threats for energy systems and the development of robust countermeasures. By anticipating and studying risks like MaDIoT and MaDIoT 3.0 attacks, projects like eFORT contribute to the security, sustainability, and resiliency of Europe’s energy systems.
Contact us
Follow us on:
