Through the digital technologies, eFORT will explore ways to use advanced digital transformation to build the next generation of smart grids, promote the efficient use of grid digital assets, give full play to the value of data, and realize the deep integration of big data, artificial intelligence and other technologies with power grid business.
The planned eFORT applications include:
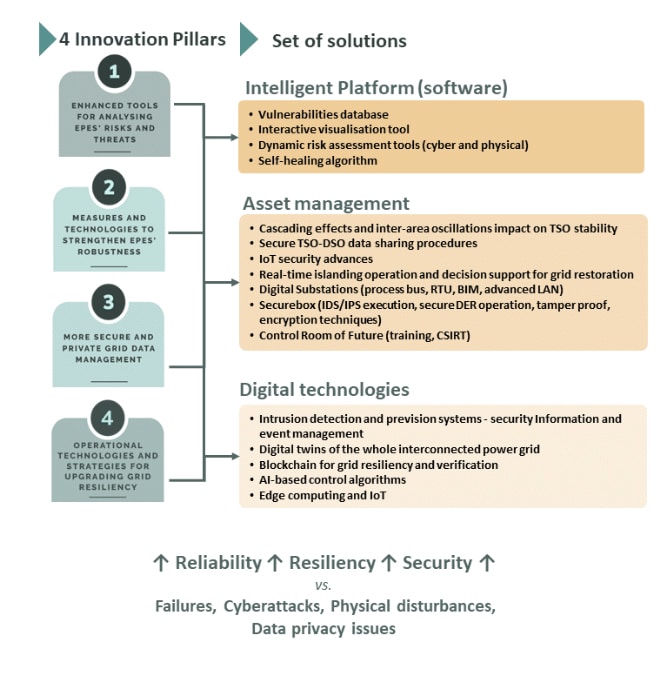
eFORT offers a comprehensive array of EPES and smart grid solutions tailored to execute asset management strategies and resilient behaviour. eFORT will ensure cost-effective long-term operations, ranging from wide area operation and mitigation schemes to load management and DER integration with advanced IoT security and decision support systems.
eFORT includes a pan European TSO-level demo site to test innovative control centres approaches; the operation of DER-intensive, islanding-prone DSO networks; digital substations; and the IoT devices for secure, resilient advanced performance of smart grid resources (SecureBox).
The SecureBox is an embedded device focused on real-time protection in a local scope (e.g., microgrid or substation).
The main functionalities of the SecureBox include:
The eFORT intelligent platform comprises the innovative software-based tools of the project and runs on extensive computational resources located in the cloud. The aim is to gather information from the field components, harmonize all resources and apply heavy-duty algorithms. Additionally, the platform will allow executing manual or pre-programmed actions over the field components.
The core components include: