Joint Stock Company “Prykarpattyaoblenergo” is a distribution system operator located in the Ivano-Frankivsk region of western Ukraine. The company’s specialists are responsible for maintaining power grids that consist of over 26,000 km of overhead and underground power lines, along with more than 6,000 transformer substations. The licensed operational area of the enterprise spans 14,000 square kilometers, through which two billion seven million kilowatt-hours of electricity are transmitted annually.
The primary task of JSC “Prykarpattyaoblenergo” is to ensure reliable and uninterrupted power supply to both the population and businesses within the region. A key factor in maintaining the quality of services is the cybersecurity of its information and operational networks. Since the onset of the ongoing conflict in Ukraine, the company’s cybersecurity department has faced numerous challenges and a significant increase in attacks.
Participation in the eFORT project represents a vital activity aimed at minimizing risks in cyberspace. Within this project, JSC “Prykarpattyaoblenergo” serves as a potential end-user of eFORT solutions and acts as a testing ground to demonstrate the effectiveness of the developed solutions.
The development of innovative solutions in the field of cybersecurity for Electrical Power and Energy Systems (EPES) necessitates a detailed study and understanding of the cyber threat landscape that an electric power company encounters daily. These activities were successfully initiated and carried out in collaboration with CIRCE, iSolutions, and JSC “Prykarpattyaoblenergo” within the framework of the eFORT project. The primary objective was to obtain and thoroughly analyze traffic from the operational networks of the Distribution System Operator (DSO) for cyber threats. The data obtained is extremely valuable and will be used in the eFORT project to guide the goals and directions of further innovative work.
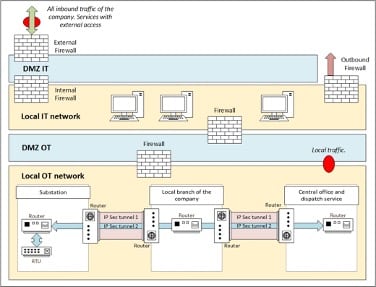
JSC “Prykarpattyaoblenergo’s” cybersecurity specialists, together with representatives from iSolutions, organized and executed traffic capture at various points in the DSO’s information and operational networks as part of the preparation for the Use Case demonstration scenarios. A substantial amount of data was collected for analysis. iSolutions provided valuable consultations and technical support for selecting the optimal network points for traffic capture. The process was divided into several stages, utilizing network devices provided by CIRCE. The data recording spanned more than a week, and the resulting data sets were handed over to CIRCE’s team of specialists, led by Esteban Damián Gutiérrez Mlot, a Computer Science Specialist at Fundación CIRCE.
The analysis of network traffic data was conducted by CIRCE using Malcolm, a powerful network traffic analysis tool suite. Malcolm automatically normalises, enriches, and correlates data for comprehensive analysis, providing robust visibility into network communications through two distinct interfaces: OpenSearch Dashboard, which offers flexible data visualisation, and Arkime, a tool designed for identifying and analysing network sessions related to suspected security incidents. For threat detection, Malcolm processes network packets through two Intrusion Detection Systems (IDS), Zeek (formerly Bro) and Suricata.
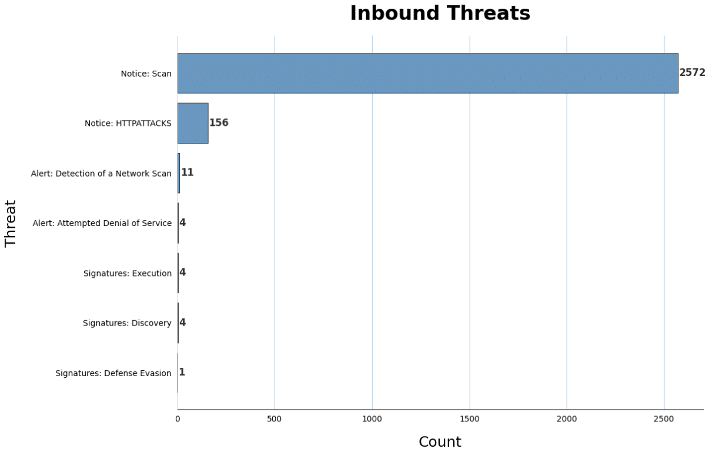
The bar chart (Figure 2) provides an overview of the attack types detected within the network traffic. The most prevalent attack category is scanning, representing a significant number of detections. Additionally, HTTP attacks show a notable frequency. These findings highlight that scanning activities, indicative of reconnaissance or probing, are the most recurrent threat, followed by a substantial number of HTTP attacks. Lower-frequency categories, such as denial of service, execution, discovery, and defence evasion, are particularly concerning. Despite their lower frequency, these less common attacks demand heightened attention due to their potential severity and specialised nature.
The outbound network serves as the gateway connecting external networks to the vital infrastructure of the electrical substation. Securing this network is paramount to safeguarding the critical processes that form the backbone of the substation’s operations.
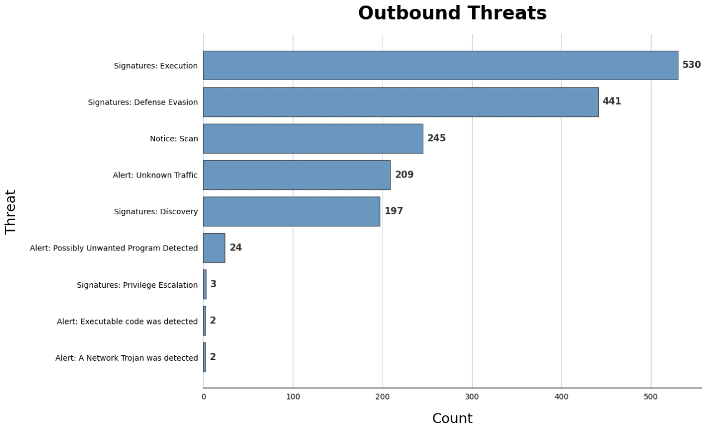
As expected, the outbound network exhibits significantly fewer threats compared to inbound traffic. Nevertheless, it is crucial to secure this area effectively, emphasizing the need for robust security measures to mitigate potential risks.
As a result of the work carried out and the deeper analysis conducted, JSC “Prykarpattyaoblenergo” has developed several technical and software measures to improve the security of the region’s power grids, which is extremely significant and important. The effective collaboration of specialists from CIRCE, iSolutions, and JSC “Prykarpattyaoblenergo” within the framework of the eFORT project has provided not only valuable contributions to the project but also advanced, innovative experiences and directions for strategic initiatives to enhance the cybersecurity of the Ukrainian DSO.
Contact us
Follow us on:
